- Disable new sign ups
- Require administrator approval for new sign ups
- Confirm user email
- User cap
- Turn on restricted access
- Minimum password length limit
- Allow or deny sign ups using specific email domains
- Set up LDAP user filter
- Enable role promotion approval
Sign-up restrictions
You can enforce the following restrictions on sign ups:
- Disable new sign ups.
- Require administrator approval for new sign ups.
- Require user email confirmation.
- Allow or deny sign ups using specific email domains.
Disable new sign ups
By default, any user visiting your GitLab domain can sign up for an account. For customers running public-facing GitLab instances, we highly recommend that you consider disabling new sign ups if you do not expect public users to sign up for an account.
To disable sign ups:
- On the left sidebar, at the bottom, select Admin.
- Select Settings > General.
- Expand Sign-up restrictions.
- Clear the Sign-up enabled checkbox, then select Save changes.
You can also disable new sign ups with the Rails console by running the following command:
::Gitlab::CurrentSettings.update!(signup_enabled: false)
Require administrator approval for new sign ups
This setting is enabled by default for new GitLab instances. When this setting is enabled, any user visiting your GitLab domain and signing up for a new account using the registration form must be explicitly approved by an administrator before they can start using their account. It is only applicable if sign ups are enabled.
To require administrator approval for new sign ups:
- On the left sidebar, at the bottom, select Admin.
- Select Settings > General.
- Expand Sign-up restrictions.
- Select the Require admin approval for new sign-ups checkbox, then select Save changes.
If an administrator disables this setting, the users in pending approval state are automatically approved in a background job.
block_auto_created_users to true in the
OmniAuth configuration or
LDAP configuration.
A user cap can also be used to enforce approvals for new users.Confirm user email
- Soft email confirmation changed from a feature flag to an application setting in GitLab 15.9.
You can send confirmation emails during sign up and require that users confirm their email address before they are allowed to sign in.
To enforce confirmation of the email address used for new sign ups:
- On the left sidebar, at the bottom, select Admin.
- Select Settings > General.
- Expand Sign-up restrictions.
- Under Email confirmation settings, select Hard.
The following settings are available:
- Hard - Send a confirmation email during sign up. New users must confirm their email address before they can sign in.
- Soft - Send a confirmation email during sign up. New users can sign in immediately, but must confirm their email in three days. After three days, the user is not able to sign in until they confirm their email.
- Off - New users can sign up without confirming their email address.
User cap
The user cap is the maximum number of billable users who can sign up or be added to a subscription without administrator approval. After the user cap is reached, users who sign up or are added must be approved by an administrator. Users can use their account only after they have been approved by an administrator.
If an administrator increases or removes the user cap, users pending approval are automatically approved.
View how to set up a user cap for groups.
1).Set a user cap
Set a user cap to restrict the number of users who can sign up without administrator approval.
The number of billable users is updated once a day.
The user cap might apply only retrospectively after the cap has already been exceeded.
To ensure the cap is enabled immediately, set the cap to a value below the current number of
billable users (for example, 1).
Prerequisites:
- You must be an administrator.
To set a user cap:
- On the left sidebar, at the bottom, select Admin.
- Select Settings > General.
- Expand Sign-up restrictions.
- Enter a number in User cap.
- Select Save changes.
Remove the user cap
Remove the user cap so that the number of new users who can sign up without administrator approval is not restricted.
After you remove the user cap, users pending approval are automatically approved.
Prerequisites:
- You must be an administrator.
To remove the user cap:
- On the left sidebar, at the bottom, select Admin.
- Select Settings > General.
- Expand Sign-up restrictions.
- Remove the number from User cap.
- Select Save changes.
Turn on restricted access
-Introduced in GitLab 17.5.
This feature is in beta.
Use restricted access to prevent overage fees. Overage fees occur when you exceed the number of seats in your subscription, and must be paid at the next quarterly reconciliation.
When you turn on restricted access, groups cannot add new billable users when there are no seats left in the subscription.
Prerequisites:
- You must have the Owner role for the group.
- The group or one of its subgroups or projects must not be shared externally.
To turn on restricted access:
- On the left sidebar, select Settings > General.
- Expand Permissions and group features.
- Under Seat controls, select Restricted access.
Known issues
When you turn on restricted access, the following known issues might occur and result in overages:
- The number of seats can still be exceeded if:
- You use SAML or SCIM to add new members, and have exceeded the number of seats in the subscription.
- Multiple users with the Owner role add members simultaneously.
- New billable members delay accepting an invitation.
- You change from using the user cap to restricted access, and have members pending approval from before you changed to restricted access. In this case, those members remain in a pending state. If pending members are approved while using restricted access, you might exceed the number of seats in your subscription.
- If you renew your subscription through the GitLab Sales Team for less users than your current
subscription, you will incur an overage fee. To avoid this fee, remove additional users before your
renewal starts. For example:
- You have 20 users.
- You renew your subscription for 15 users.
- You will be charged overages for the five additional users.
Minimum password length limit
You can change the minimum number of characters a user must have in their password using the GitLab UI.
Password complexity requirements
- Introduced in GitLab 15.2.
By default, the only requirement for user passwords is minimum password length. You can add additional complexity requirements. Changes to password complexity requirements apply to new passwords:
- For new users that sign up.
- For existing users that reset their password.
Existing passwords are unaffected. To change password complexity requirements:
- On the left sidebar, at the bottom, select Admin.
- Select Settings > General.
- Expand Sign-up restrictions.
- Under Minimum password length (number of characters), select additional password complexity requirements. You can require numbers, uppercase letters, lowercase letters, and symbols.
- Select Save changes.
Allow or deny sign ups using specific email domains
You can specify an inclusive or exclusive list of email domains which can be used for user sign up.
These restrictions are only applied during sign up from an external user. An administrator can add a user through the administrator panel with a disallowed domain. The users can also change their email addresses to disallowed domains after sign up.
Allowlist email domains
You can restrict users only to sign up using email addresses matching the given domains list.
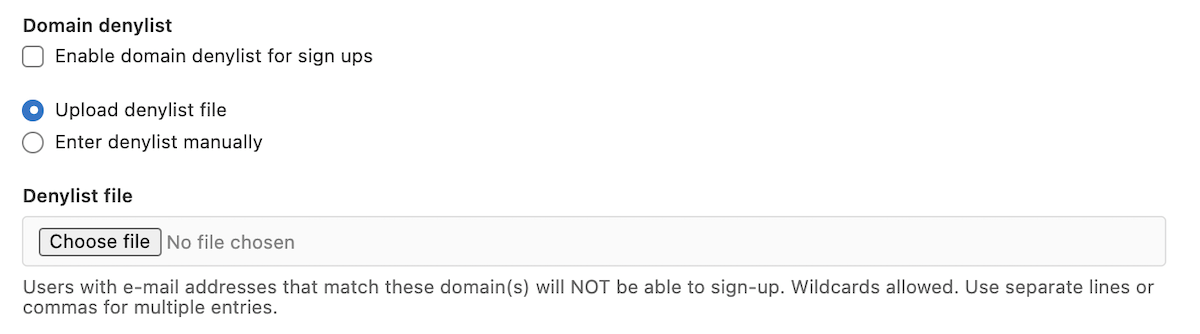
Denylist email domains
You can block users from signing up when using an email addresses of specific domains. This can reduce the risk of malicious users creating spam accounts with disposable email addresses.
Create email domain allowlist or denylist
To create an email domain allowlist or denylist:
- On the left sidebar, at the bottom, select Admin.
- Select Settings > General.
- Expand Sign-up restrictions.
-
For the allowlist, you must enter the list manually. For the denylist, you can enter the list manually or upload a
.txtfile that contains list entries.Both the allowlist and denylist accept wildcards. For example, you can use
*.company.comto accept everycompany.comsubdomain, or*.ioto block all domains ending in.io. Domains must be separated by a whitespace, semicolon, comma, or a new line.
Set up LDAP user filter
You can limit GitLab access to a subset of the LDAP users on your LDAP server.
See the documentation on setting up an LDAP user filter for more information.
Enable role promotion approval
-
Introduced in GitLab 16.9 with a flag named
member_promotion_management. - Feature flag
member_promotion_managementchanged fromwiptobetaand enabled by default in GitLab 17.5.
In the Ultimate tier, non billable roles, can be promoted to a billable role in any Project or Group, resulting in the increase of billable seats, without admins having any control on this promotion. To prevent existing users of the subscription from being promoted to a billable role, you can enable role promotion approval.
When this setting is enabled, any existing user of the subscription when added to a group or project on a billable role will be pending administrator approval.
Promotions or updates of user roles for users that already occupy a billable seat do not require administrator approval.
If the user is added to a group or project by an administrator, any membership requests for this user to any other group or project will be approved automatically.
To enable role promotion approval:
- On the left sidebar, at the bottom, select Admin.
- Select Settings > General.
- Expand Sign-up restrictions.
- In the Seat controls section, select Approve role promotions.
Known issues
When you turn on role promotion approval, the billable count can still increase if a user requests access to a group and is approved by the group Owner on a billable role.