Installing GitLab on Google Cloud Platform
You can install GitLab on a Google Cloud Platform (GCP) using the official Linux package. You should customize it to accommodate your needs.
Click to Deploy steps
It’s an alternative to using a GCP VM, and uses
the Cloud native GitLab Helm chart.Prerequisites
There are two prerequisites to install GitLab on GCP:
- You must have a Google account.
- You must sign up for the GCP program. If this is your first time, Google gives you $300 credit for free to consume over a 60-day period.
After you have performed those two steps, you can create a VM.
Creating the VM
To deploy GitLab on GCP you must create a virtual machine:
- Go to https://console.cloud.google.com/compute/instances and sign in with your Google credentials.
-
Select Create
-
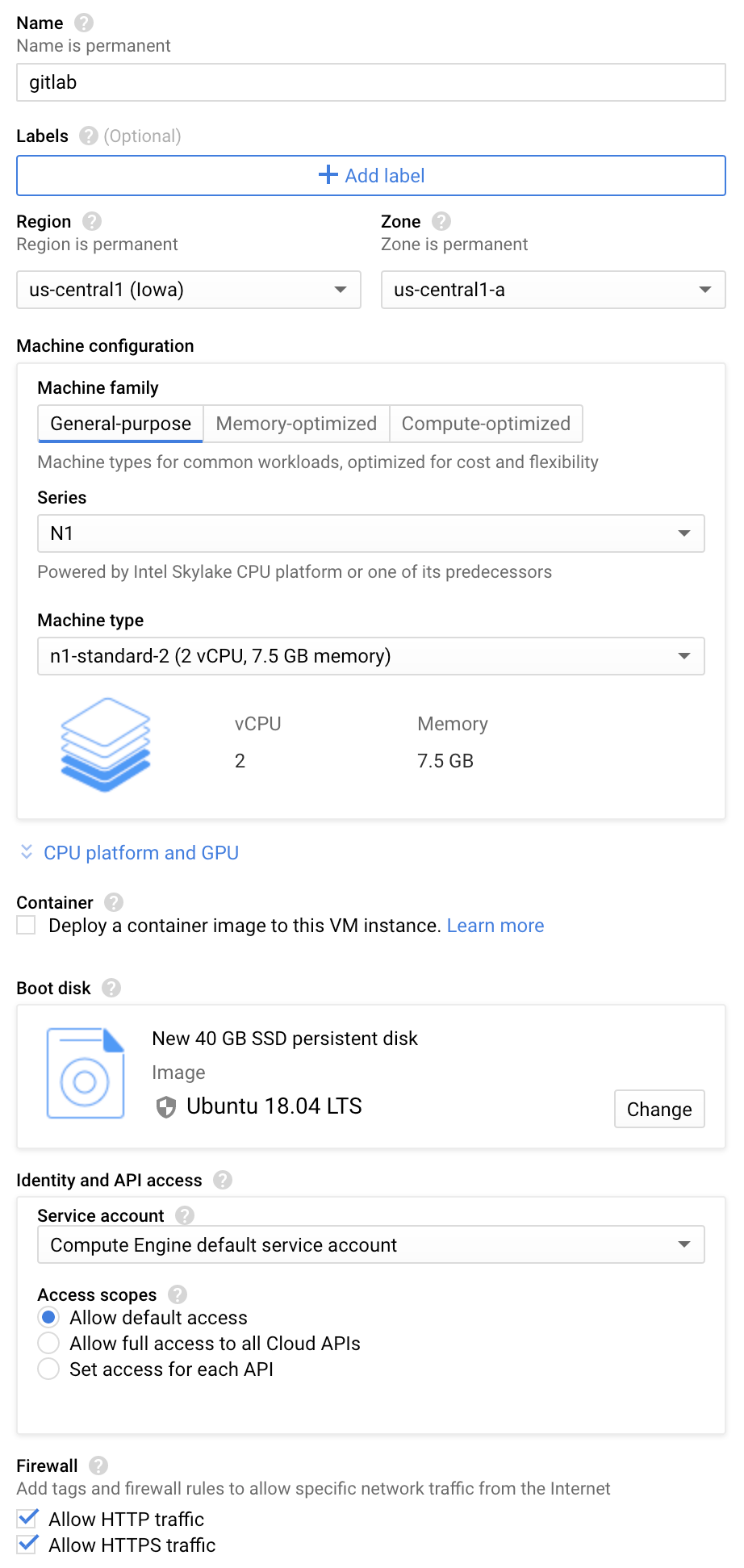
On the next page, you can select the type of VM as well as the estimated costs. Provide the name of the instance, desired data center, and machine type. Note our hardware requirements for different user base sizes.
-
To select the size, type, and desired operating system, select Change under
Boot disk. select Select when finished. - As a last step allow HTTP and HTTPS traffic, then select Create. The process finishes in a few seconds.
Installing GitLab
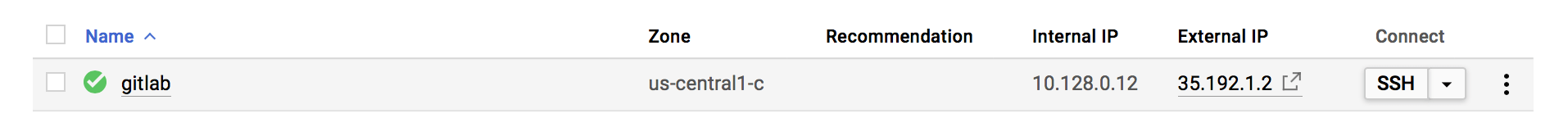
After a few seconds, the instance is created and available to sign in. The next step is to install GitLab onto the instance.
- Make a note of the external IP address of the instance, as you will need that in a later step.
- Select SSH under the connect column to connect to the instance.
-
A new window appears, with you logged into the instance.
-
Next, follow the instructions for installing GitLab for the operating system you choose, at https://about.gitlab.com/install/. You can use the external IP address you noted before as the hostname.
-
Congratulations! GitLab is now installed and you can access it via your browser. To finish installation, open the URL in your browser and provide the initial administrator password. The username for this account is
root.
Next steps
These are the most important next steps to take after you installed GitLab for the first time.
Assigning a static IP
By default, Google assigns an ephemeral IP to your instance. It is strongly recommended to assign a static IP if you are using GitLab in production and use a domain name as shown below.
Read Google’s documentation on how to promote an ephemeral IP address.
Using a domain name
Assuming you have a domain name in your possession and you have correctly set up DNS to point to the static IP you configured in the previous step, here’s how you configure GitLab to be aware of the change:
-
SSH into the VM. You can select SSH in the Google console and a new window pops up.
In the future you might want to set up connecting with an SSH key instead.
-
Edit the configuration file of the Linux package using your favorite text editor:
sudo vim /etc/gitlab/gitlab.rb -
Set the
external_urlvalue to the domain name you wish GitLab to have withouthttps:external_url 'http://gitlab.example.com'We will set up HTTPS in the next step, no need to do this now.
-
Reconfigure GitLab for the changes to take effect:
sudo gitlab-ctl reconfigure -
You can now visit GitLab using the domain name.
Configuring HTTPS with the domain name
Although not needed, it’s strongly recommended to secure GitLab with a TLS certificate.
Configuring the email SMTP settings
You must configure the email SMTP settings correctly otherwise GitLab cannot send notification emails, like comments, and password changes. Check the Linux package documentation how to do so.
Further reading
GitLab can be configured to authenticate with other OAuth providers, like LDAP, SAML, and Kerberos. Here are some documents you might be interested in reading: